Description
This was a result of a small code-review that me, @fjreis , @r0t) did to some of the TOP Joomla plugins officially listed. This time we decided to look for low-hanging fruits, and we came up with this instance of XSS. This cross-site script issue posed Hikashop’s users to a low risk as it could only be exploited from the Hikashop’s control panel. Nevertheless, we decided to report it and HikaShop kindly fixed the issue and assigned a CVE identifier to it.
Proof of concept
Joomla has its methods to deal with user’s input. As we were targeting low-hanging fruits, we decided to find out how user’s input data were being handled by HikaShop. For this, apart of other searches, we searched for occurrences of the JRequests::GetString method.
Information obtained in the documentation showed the following description:
Fetches and returns a given filtered variable. The string filter deletes ‘bad’ HTML code, if not overridden by the mask. This is currently only a proxy function for getVar().
As sated above, removing ‘bad’ HTML code meant that tags such <script>, <img onerror=, or <svg onload= will not be returned by the function. However, further investigation showed the function displayStateDropDown which is responsible for creating a <select> tag with the attributes provided by the parameters.
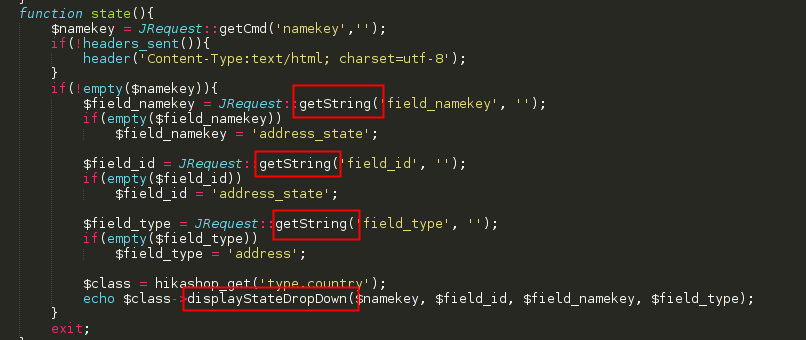
Looking at the code above, it was possible to understand that HikaShop was expecting at least three different parameters, named: field_namekey, field_id and field_type. As it was not specified in the code, this parameters could be submitted using a GET or a POST request.
A way to exploit this issue was to inject the JavaScript code “onmouseover%3d”alert(‘XSS’)” in any of the three vulnerable parameters. This resulted in the following GET request:
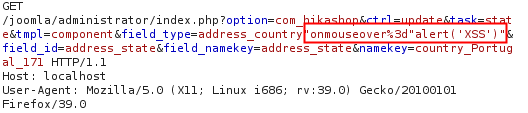
GET Request
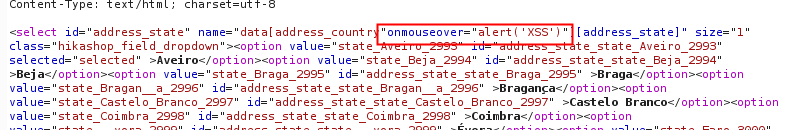
Response with injected payload
The original url request was:
https://joomla url/administrator/index.php?option=com_hikashop&ctrl=update&task=state&tmpl=component &field_type=address_country&field_id=address_state&field_namekey=address_state&namekey=country_Portugal_171
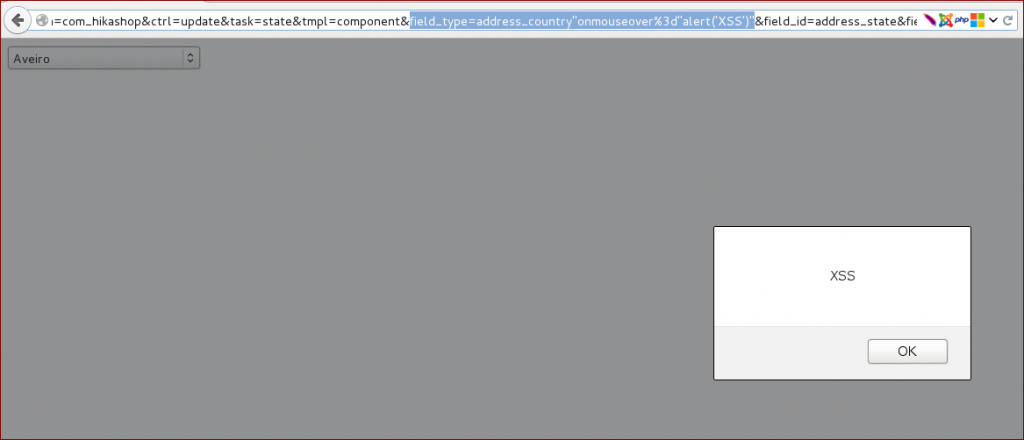
As a result, the malicious JavaScript code was executed in the context of the victim’s session..
Release notes
Minor security issue allowing reflected XSS in the backend has been fixed. Reported by Vitor Oliveira, Filipe Reis and Fábio Pires from Integrity (https://labs.integrity.pt/)
Release notes can be found here.
Report timeline
- September 01, 2015 — Bug reported to HikaShop
- September 01, 2015 — HikaShop’s team replied asking for more info.
- September 24, 2015 — Bug fixed
- October 05, 2015 — Public disclosure
Affects
- 2.5.x
Fixed in version 2.6.0