Description
Back in 2015, while navigating in the interwebz, I came across a product called osTicket. osTicket was announced as a widely-used and trusted open source support ticket system. It seamlessly routed inquiries created via email, web-forms and phone calls into a simple, easy-to-use, multi-user, web-based customer support platform.
This software was also used by IPLeiria (my college in that period), so the challenge of pwning it increased a little bit. (No, Mr. agent, I didn’t hack into my school. You can go now.  )
)
After downloading the latest version to a VM and realise how it works, I was able to discover an Insecure Direct Object Reference vulnerability.
Proof of concept
The software was simple. In this case, a simple web form that allowed me to create tickets and attach files to them.
While I was intercepting the traffic, I noticed that it was possible to submit tickets with an empty Issue Summary field, but a file attached to the form. Although the software returned an error message saying Issue Summary is a required field, the file was still uploaded, and an attach ID was still assigned to it.
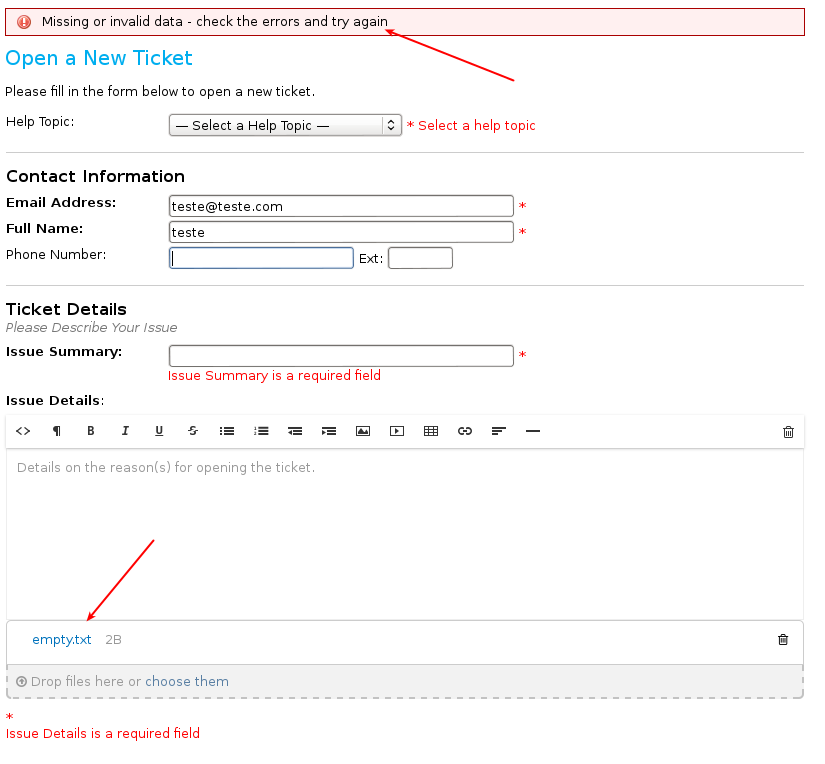
Filled form after submission
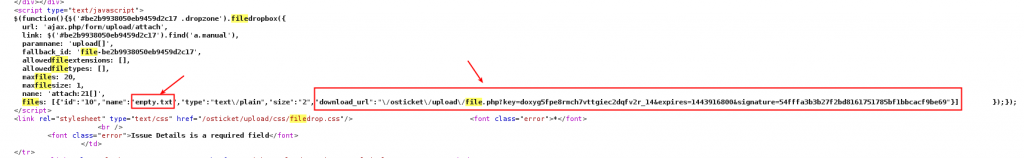
In the error page above, I noticed that the attached file was a hyperlink, and this hyperlink allowed me to download the file. The URL was composed by three parameters: the key, the expiration and a signature. Without this parameters, it would not be possible to download this file.
A close look at the intercepted traffic revealed two different POST requests. The first was responsible for sending the file to the server, returning the ID associated with that file. (In this case, the ID was 10)
The second request associated the ID (10), to the draft ticket that was being created. The image below shows an extract of the POST request described above.
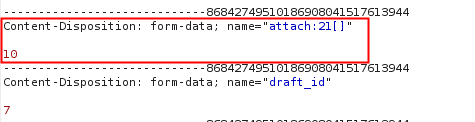
Request sent to /osticket/upload/open.php
The response to this request returned a JavaScript code that was responsible for creating the hyperlink mentioned above. This JavaScript code included the necessary information to download the attached file.
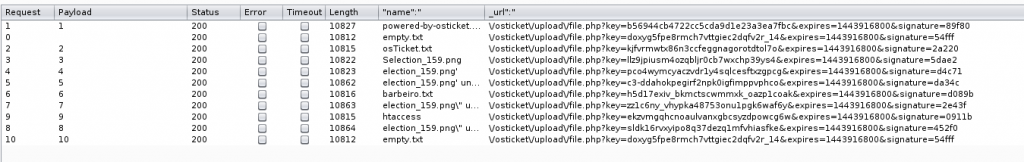
Automating this process using Burp Intruder, it was possible to send multiple request with different ID’s, and obtain all the files uploaded to the server.
It should also be noted that this vulnerability was exploited without authentication and, as it was a draft ticket, there was a huge possibility that this attack would be invisible to the support team.
Furthermore, there’s a high probability that ticket attachments contained sensitive information to the user, increasing the impact of this issue.
Report timeline
- September 30, 2015 — “Where to report” mail sent to osTicket
- October 02, 2015 — osTicket’s SupportSystem Team reply with: “Thanks for your email. You can report any findings on our GitHub project page. Thanks! ”
- October 02, 2015 — Bug reported to osTicket’s github project page.
- October 03, 2015 — Bug fixed.
- October 04, 2015 — Fix merged to dev release.
- October 04, 2015 — Public disclosure.
Affects
- 1.8.x
- 1.9.x (until 1.9.13)
Fixed in version 1.9.13